Power BI Architecture: Learn How to work on Data Security
Microsoft’s data visualization, reporting, and analytics products and services are together referred to as Power BI. Power BI Architecture can import data from many sources and organize it so that it can be used to execute queries, create reporting dashboards, and visualize data. There are a variety of Power BI components available for various platforms and uses. In this article, we want to explain Power BI Architecture, Data Storage Security, User Authentication, and more.
Join the Best Power BI Training in Chennai with IBM Certification at Softlogic Systems to become a master in data visualization.
What is Power BI Architecture?
Built on Azure, Microsoft’s cloud computing infrastructure is the Power BI service. There are numerous active deployments of Power BI that are currently made available to customers in the regions those data centers serve, as well as an equal number of passive deployments that act as backups for each active deployment.
Power BI Architecture is currently deployed in numerous data centers throughout the world.
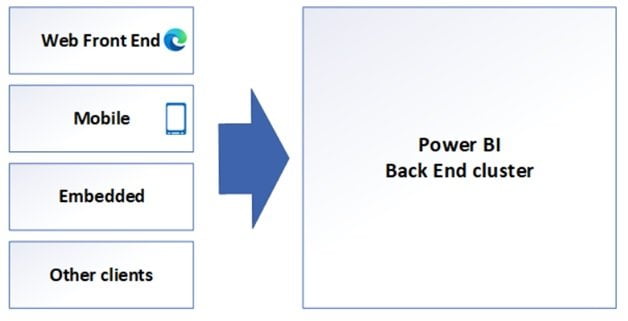
Web Front-End Cluster
When a user loads a website, the WFE cluster sends the user’s browser the initial HTML page contents as well as links to CDN content that is utilized to render the website in the user’s browser.
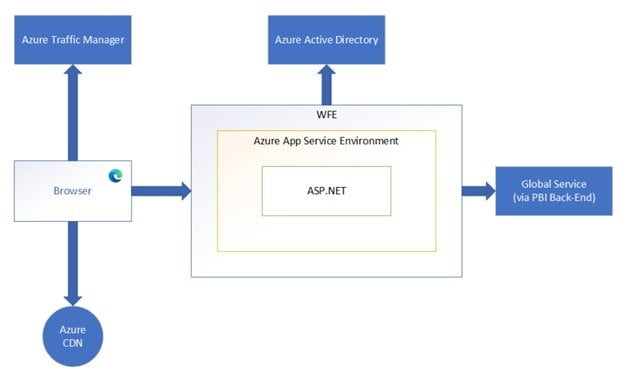
An ASP.NET website running in the Azure App Service Environment makes up a WFE cluster. The client’s DNS service may get in touch with Azure Traffic Manager when users try to connect to the Power BI service to determine the best (often closest) datacenter for their needs. See the Performance traffic-routing method for Azure Traffic Manager for further details on this procedure.
The majority of static resources, including *.js, *.css, and image files, are kept on the Azure Content Delivery Network (CDN) and are downloaded by the browser directly. For compliance purposes, Sovereign Government cluster deployments are an exception to this rule and will host static content on a WFE cluster from an area that complies with the requirements rather than using a CDN.
Back End Cluster of Power BI Architecture
The backbone of all the capabilities offered by Power BI is the back-end cluster. It is made up of a number of service endpoints that are used by Web Front End and API clients as well as background running services, databases, caches, and several other parts.
Most Azure regions have access to the back end, and more regions are being deployed as they become available. Once the vertical and horizontal scaling constraints of a single cluster are reached, one or more back-end clusters hosted by a single Azure region provide infinite horizontal scaling of the Power BI service.
Each stateful back-end cluster houses all of the data belonging to each tenant assigned to that cluster. The tenant’s home cluster is a cluster that houses all of a particular tenant’s data. The Web Front End routes requests to a tenant’s home cluster using information about the user’s home cluster that Global Service provides to authenticated users.
Stateful resources like SQL databases, storage accounts, service buses, caches, and other essential cloud components are bundled into various resizable-scale sets suited for executing specific tasks for each back-end cluster.
Except for data replication to a secondary back-end cluster in a paired Azure region in the same Azure geography, tenant information and data are retained within cluster limitations. In the event of a regional outage, the secondary back-end cluster acts as a failover cluster and is otherwise inactive.
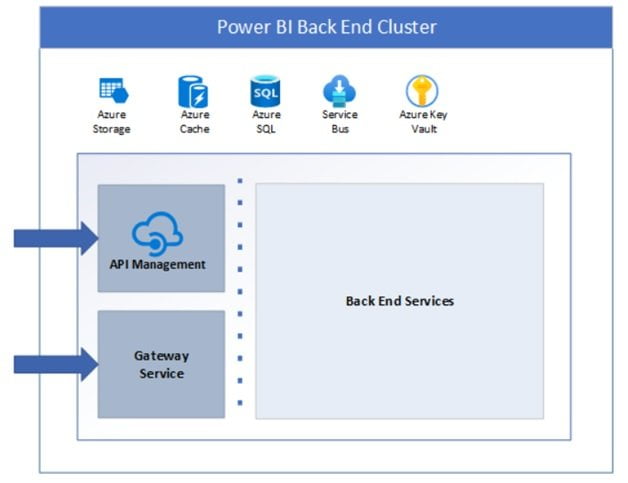
Except for two components that may be accessed from the public internet, the cluster’s back-end functionality is provided by micro-services running on several workstations inside the cluster’s virtual network.
- Gateway Service
- Azure API Management
Data Storage Security
Two main repositories are used by the Power BI architecture to store and manage knowledge.
The data that users submit is frequently transmitted to Azure BLOB storage, and all other data as well as system artifacts are kept in Azure SQL information.
The line within the back-end cluster image—which can be seen in the preceding section on the left of the dotted line—defines the distinction between roles that are only available by the system and the two elements that are only accessible by users.
The gateway role accepts and manages any requests made by the consumer after an associated documented user connects to the service, with Azure API Management eventually taking over the management of the association and any requests.
This then engages with the rest of the Service on the user’s behalf. A consumer’s effort to view a dashboard is also followed by the gateway role accepting the request and sending a letter of invitation to the presentation role so that it can obtain the data needed by the browser to create the dashboard.
User Authentication
Users log in to the service via the email address used to establish their Power BI Services account.
The architecture of Power BI users that login email because of the effective username, which is passed to resources whenever a user makes an attempt to access a piece of information. The effective username is mapped to a User Principal Name (UPN) and all resolutions associated with the windows domain account apply to it.
The efficient username to UPN mapping is simple for businesses who use work emails (like [email protected]) for Power BI architecture login. A mapping between the AAD and on-premises credentials would compel directory synchronization for companies who don’t utilize work emails for Power BI architecture login.
Platform security for Power BI architecture encompasses network security, multi-tenant environment security, and the flexibility to implement additional AAD-based security mechanisms.
Data & Repair Security
As mentioned earlier in this article, the on-premises Active Directory servers use a user’s Power BI architectural login to translate to a UPN for credentials. It’s important to remember that users are accountable for the information they post. The users with whom the dashboard is shared cannot be given access to the report if a user connected to data sources misuses her credentials and shares a report using that data.
The connection to SQL Server Associate Analysis Services is an exception to this rule. The user attempting to access the report must first authenticate in order to access any underlying reports or data sets. And only if the user has extra credentials to access the information may access be given.
Conclusion
Power BI architecture is an Azure service. Power BI can access a variety of data sources. On the dataset, Power BI Desktop enables you to create reports and data visualizations. Power BI gateway is linked to on-premise data sources to obtain complete data for reporting and analytics. Learn to create compelling visualizations by enrolling in our Power BI Training in Chennai at Softlogic Systems.