Network Security Fundamentals for Newbies
This is an intellectual era. Businesses today are more technologically sophisticated than ever before, and as technology improves, so must companies’ security postures.
With so many devices connecting with one another over wired, wireless, or cellular networks, network security is now a critical concept.
In this essay, we’ll look at the concept of network security as well as its key properties.
Learn Cybersecurity Course in Chennai with IBM Certification at Softlogic Systems.
Network security – What is it?
Network security is the process of taking safeguards to protect the underlying networking infrastructure against unauthorized access, misuse, malfunction, alteration, destruction, or unlawful disclosure.
Without a doubt, the Internet has taken up a substantial chunk of our time.
A huge percentage of people’s professional, social, and personal activities are now conducted online. But how safe is your network?
Numerous individuals attempt to hack into our Internet-connected computers, steal our privacy, and stop us from utilizing Internet services.
Due to the frequency, variety, and possibility for new and more devastating attacks in the future, network security has become a crucial concern in the field of cybersecurity.
Computers, users, and applications can operate in a secure environment while carrying out their assigned, essential tasks by putting network security procedures in place.
How can network security be ensured?
Strong and complex passwords must be used everywhere, not just on individual computers within an organization, but also throughout the network.
These passwords cannot be easy to guess, simple, or default. This easy action can make a big difference in how secure your networks are.
Why is a security essential?
Information security plays important responsibilities like:
- The organization’s ability to conduct business without interruption
- Enabling the secure use of applications installed on the IT systems of the organization
- Securing the data that the organization gathers and utilizes
What varieties of network security are there?
- Access Management
- Firewalls
- Application security
- Virtual Private Network (VPN)
- Wireless Security
- Intrusion Prevention System
- Behavioral Analytics
What is a network security attack?
Any technique, procedure, or tool used to maliciously try to breach network security is referred to as a “network attack.” Network security is the process of preventing network attacks across specific network infrastructure, but the attacker’s strategies and methods further identify whether the attack is an active cyberattack, a passive attack, or a combination of the two.
Active Attack
A network exploits that involve an active attack is one in which the attacker tries to alter data that is already on the target or that is being sent to the target.
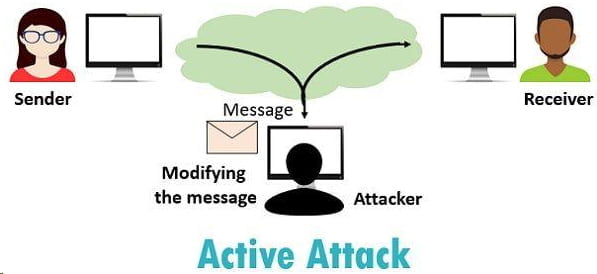
Distance is a barrier to communication between the sender and the receiver. Therefore, Sender uses an insecure network to deliver an email to the recipient.
On the same network, there is an attacker. Now that the network’s data flow is accessible to all users, an attacker can change a little piece of an allowed message to cause an illegal outcome.
A notification that reads “Allow Ron to read confidential file X” might instead read “Allow Robert to read confidential file X,” for instance.
Active network assaults are frequently aggressive, blatant attacks that their victims are aware of as soon as they happen.
Active attacks are incredibly harmful in nature and frequently lock out users, corrupt memory or files, or forcibly enter a targeted device or network.
Passive Attack
A passive attack is a network attack that monitors a system and occasionally scans it for open ports and security holes without affecting the system’s resources.
Let’s think about the earlier illustration:
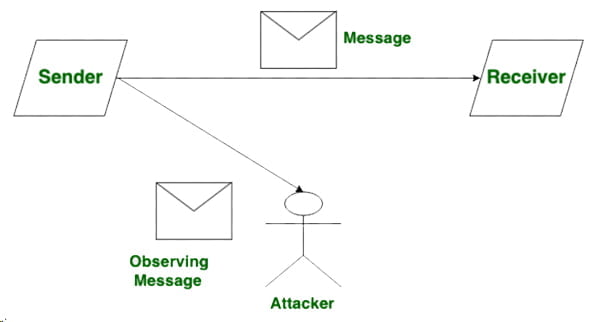
A network that is vulnerable to assaults is used by the Sender to transmit an email to the recipient.
The attacker on the same network keeps an eye on the data transmission happening between the Sender and the Receiver.
Consider a scenario where the sender gives the recipient some sensitive data, such as bank account information, in plain text. Data can be easily accessed by an attacker who will use it maliciously.
Therefore, the objective of a passive assault is to penetrate a computer system or network and gather data covertly.
To protect the underlying network architecture, various hardware and software solutions must be implemented.
You can identify new threats before they breach your network and compromise your data if you have the right network security measures in place.
What kinds of network security are there?
A network security system is made up of several components that all work together to improve your security position.
The following section discusses the most common network security elements.
Access Control : To keep potential attackers out, you should be able to block unauthorized users and devices from connecting to your network.
Users who are granted network access should only be able to access the resources for which they have been granted permission.
Application Security : It refers to the tools, processes, and procedures that can be used to find and patch application defects that hackers could use to gain access to your network.
Firewalls : A firewall is a piece of hardware or a service that regulates network access.
They use a set of established regulations to allow or ban traffic. Software and hardware are the parts of firewall.
Virtual Private Network (VPN) : A virtual private network encrypts the connection between an endpoint and a network, which is commonly the Internet.
This method authenticates communication between a device and a secure network, establishing a safe, encrypted “tunnel” across the public internet.
Behavioral Analytics : You must be familiar with usual network behavior in order to detect anomalies or network breaches as they occur. Behavioral analytics tools detect out-of-the-ordinary behavior automatically.
Wireless security : Wireless networks are less secure than conventional networks. Cybercriminals are increasingly targeting mobile apps and gadgets. As a result, you must restrict the devices that can connect to your network.
Intrusion Prevention System (IPS) : These systems analyze network traffic to detect and prevent attacks, often by comparing network activity signatures to repositories of well-known attack vectors.
The following are some ways for implementing network security. In addition to these, you’ll need a number of software and hardware tools to assure network security, including the following:
- Firewalls
- Packet crafters
- Web scanners
- Packet sniffers
- Intrusion detection system
- Penetration testing software
Network security is critical for overall cybersecurity since the network acts as a significant line of defense against external threats.
Strong network security avoids data breaches because practically all data and apps are network-connected.
Network Security Jobs
Businesses are spending more money than ever before to recruit highly qualified cybersecurity specialists to secure their most sensitive assets as a result of the well reported success of well-known cyberattacks such as WannaCry and Adylkuzz.
The two highest-paying cybersecurity occupations are network security analyst and network security engineer.
A network security analyst is more likely to be tasked with scanning the network for potentially exploitable flaws, whereas a network security engineer is more likely to be tasked with designing security methods.
The typical salary for both positions is between $90,000 and $150,000.
Conclusion
Check out our Cybersecurity Certification Training in Chennai with IBM Certification at Softlogic Systems if you want to understand cybersecurity and have a vibrant career in the field.
This program will provide you with a solid grasp of cybersecurity as well as expertise of the topic.

