Basics of Cybersecurity for Beginners
Cybercrime is a topic that has received a lot of attention recently. It endangers not only personal security but also huge international organizations, banks, and governments. Large organized crime rings now function like start-ups, using highly trained coders who are constantly developing new cyberattacks. Today’s organized cybercrime significantly outnumbers the past’s shadow lone hackers. Because there is so much data that could be exploited, cybersecurity has grown in importance. As a result, we’ve decided to write this blog post regarding “What Is Cybersecurity?” Softlogic Systems offers the Best Cybersecurity Courses in Chennai with IBM Certification.
Why Cybersecurity is the need of the hour?
It’s fair to say that today’s age relies heavily on the internet, and most internet users have little to no idea how that innocuous 1s and 0s make their way safely to our computers. It’s the perfect time to be a hacker. Black hat hackers are having a very difficult time finding vulnerabilities and developing malicious software for them because there are so many access points, public IP addresses, continual traffic, and loads of data to attack. In addition, cyberattacks are developing daily. Many people still don’t understand how hackers get around firewalls and virus scanners even though their software is getting smarter and more inventive.

As a result, we need some kind of mechanism that safeguards us from all these hacks and ensures that our data doesn’t end up in the wrong hands. This is precisely why we need cybersecurity, and the best way to learn about it is to enroll in a master’s program in cybersecurity.
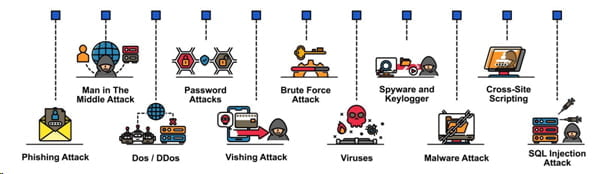
Types of Cyberattacks
Overview of Cybersecurity
The term “cybersecurity” describes a group of methods used to safeguard the integrity of networks, programs, and data against damage, attack, or illegal access.
Security from the perspective of computing includes both cybersecurity and physical security, both of which are employed by businesses to prevent illegal access to data centers and other computerized systems. Cybersecurity is a subset of information security, which aims to protect the availability, confidentiality, and integrity of data. Utilizing cyber security can assist manage risk and prevent cyberattacks, data breaches, and identity theft.
Therefore, one can query “What are we trying to protect ourselves against” when discussing cybersecurity. The three key areas we are attempting to govern are as follows:
- Unauthorized Access
- Unauthorized Removal
- Unauthorized modifications
These three phrases are interchangeable with the well-known CIA triad, which stands for availability, confidentiality, and integrity. The majority of an organization’s security policies are based on these three tenets, which are also known as the CIA triad or the three pillars of security.
The CIA Triad
The Confidentiality, Integrity, and Availability (CIA) triangle is a design framework that helps businesses and organizations create their security policies. To prevent confusion with the Central Intelligence Agency, it is also known as the AIC trio (CIA). The triad’s elements are thought to be the most crucial and fundamental parts of security. So allow me to give you a quick overview of the three parts.
Confidentiality
The protection of personal data is confidentiality. Confidentiality refers to not disclosing client information to anybody else, including co-workers, friends, family, etc.
- Data encryption breaking
- Assaults using a man in the middle on simple text
- Sensitive data theft or unauthorized copying
- Putting malicious software or spyware on a server
Integrity
When referring to computer systems, the term “integrity” describes procedures for guaranteeing that data is authentic, accurate, and protected from unauthorized user modification.
- Malware infiltration through online penetration
- Unauthorized access to servers and record tampering
- Scanning unauthorized databases
- Remote management of zombie systems
Availability
In the context of a computer system, availability refers to a user’s ability to access data or resources in the right location and format.
- Attacks by DOS/DDoS
- Ransomware attacks: Compulsory key data encryption
- Intentionally tampering with a server room’s power supply
- Overwhelming a server with requests
How are Cybersecurity Measures Adopted?
There are many methods for putting cybersecurity into practice, but there are three key phases for resolving a security-related problem.
Recognizing the issue that is creating the security issue is the first step. For instance, we must determine whether a man-in-the-middle attack or a denial-of-service assault is taking place. The problem must next be assessed and examined. We must ensure that all the data and information that might have been exposed during the attack is isolated. The last step after assessing and studying the issue is to create a patch that really fixes it and returns the organization to a functioning state.
Three principles are kept in mind for various calculations when identifying, analyzing, and treating a cyberattack. As follows :
- Vulnerability
- Threat
- Risk
Vulnerability
The term “vulnerability” describes a weak point in an asset that one or more attackers could take advantage of.
In the context of the cyber world, a vulnerability is a flaw or error in software or hardware that has not yet been patched and is likely to be used to harm one of the components of the CIA triumvirate.
Threat
Any occurrence that could endanger a person or an organization is considered a threat. Risks from the environment, malicious people, and accidental people. Threat assessment methods are employed to comprehend dangers.
Risk
Risk is the possibility of loss or damage when a threat takes advantage of a vulnerability.
Threat + Vulnerability = Risk
Managing risks is essential to cybersecurity.
Conclusion
Check out our Cybersecurity Certification Training in Chennai in Collaboration with IBM if you want to understand cybersecurity and develop a vibrant career in the field. This program combines classroom instruction with instructor-led live training and real-world project experience. You will gain a thorough understanding of cybersecurity and mastery of the subject thanks to this program.